MITRE Frameworks
Table of Contents

Frameworks are heavily relied upon across many industries. Often a framework is built upon best practice and expert knowledge to serve as the groundwork for others to follow, dramatically reducing the number of resources and time required for internal development. Some frameworks are open-source; others are proprietary. Either way, if an organization is adopting a particular framework, they’re anticipating that the framework will help dictate operational aspects of the business, help find inadequacies, or serve to assist in meeting specific regulatory or compliance requirements. Without community frameworks, organizations (especially smaller ones) would be lost trying to find their way on their own.
Additionally, frameworks allow multiple parties to speak and understand information by introducing a form of a standard to follow. In business communication, it’s much easier for an organization to say “We use X framework” and present supporting data than it is for an organization to explain their home-grown methods of doing things and the justifications behind every decision made.
In the case of Information Security, a few different frameworks can help an organization improve its Cybersecurity program and defense posture. Today we will review a few frameworks developed by MITRE, reviewing what they are and how Cybersecurity programs can use them.
MITRE ATT&CK
The ATT&CK framework is perhaps MITRE’s most well-known product. Initially published in 2013, the ATT&CK framework was designed to identify attacker methodologies and build a complete picture of how cybersecurity attacks transpire, from start to finish, based on actual-world attacks and adversaries (Anomali, n.d.). ATT&CK is an acronym that does a reasonably good job self-explaining what it pertains to: Adversarial Tactics, Techniques, and Common Knowledge. It focuses on identifying tactics used as categories to build a comprehensive list of techniques at its core. And since these are created based on actual attacks, you can find out which adversaries utilize which tactics and techniques. The beauty of it is you can start with a named APT group, tactic, or technique and find all the information you need through the ‘matrices’ of ATT&CK.
The list of tactics MITRE compiled for ATT&CK is broken down between either ‘Enterprise’ or ‘Mobile. Today, we will be focusing strictly on the Enterprise category, so this post might be excluding some mobile-specific information.
Under Enterprise today, there are 14 tactics, each with a referential Tactic ID, Name, and Description.
| ID | Name | Description |
|---|---|---|
| TA0043 | Reconnaissance | The adversary is trying to gather information they can use to plan future operations. |
| TA0042 | Resource Development | The adversary is trying to establish resources they can use to support operations. |
| TA0001 | Initial Access | The adversary is trying to get into your network. |
| TA0002 | Execution | The adversary is trying to run malicious code. |
| TA0003 | Persistence | The adversary is trying to maintain their foothold. |
| TA0004 | Privilege Escalation | The adversary is trying to gain higher-level permissions. |
| TA0005 | Defense Evasion | The adversary is trying to avoid being detected. |
| TA0006 | Credential Access | The adversary is trying to steal account names and passwords. |
| TA0007 | Discovery | The adversary is trying to figure out your environment. |
| TA0008 | Lateral Movement | The adversary is trying to move through your environment. |
| TA0009 | Collection | The adversary is trying to gather data of interest to their goal. |
| TA0011 | Command and Control | The adversary is trying to communicate with compromised systems to control them. |
| TA0010 | Exfiltration | The adversary is trying to steal data. |
| TA0040 | Impact | The adversary is trying to manipulate, interrupt, or destroy your systems and data. |
You can think of the tactics as things an adversary may do when attacking an organization, but it still doesn’t explain how they do it. This is where techniques come into play. Each tactic contains dozens of techniques that demonstrate how an adversary can achieve the tactic. You can see a complete list of all 188 techniques on MITRE’s website here: https://attack.mitre.org/techniques/enterprise/. Notice these are further broken down into sub techniques as well! Each one comes with specific examples for how an adversary behaves and includes ways in which defenders can detect or mitigate each technique! Of course, everything comes with a handy reference ID you can point to when communicating or documenting procedures, and everything is linkable directly from the ATT&CK website.
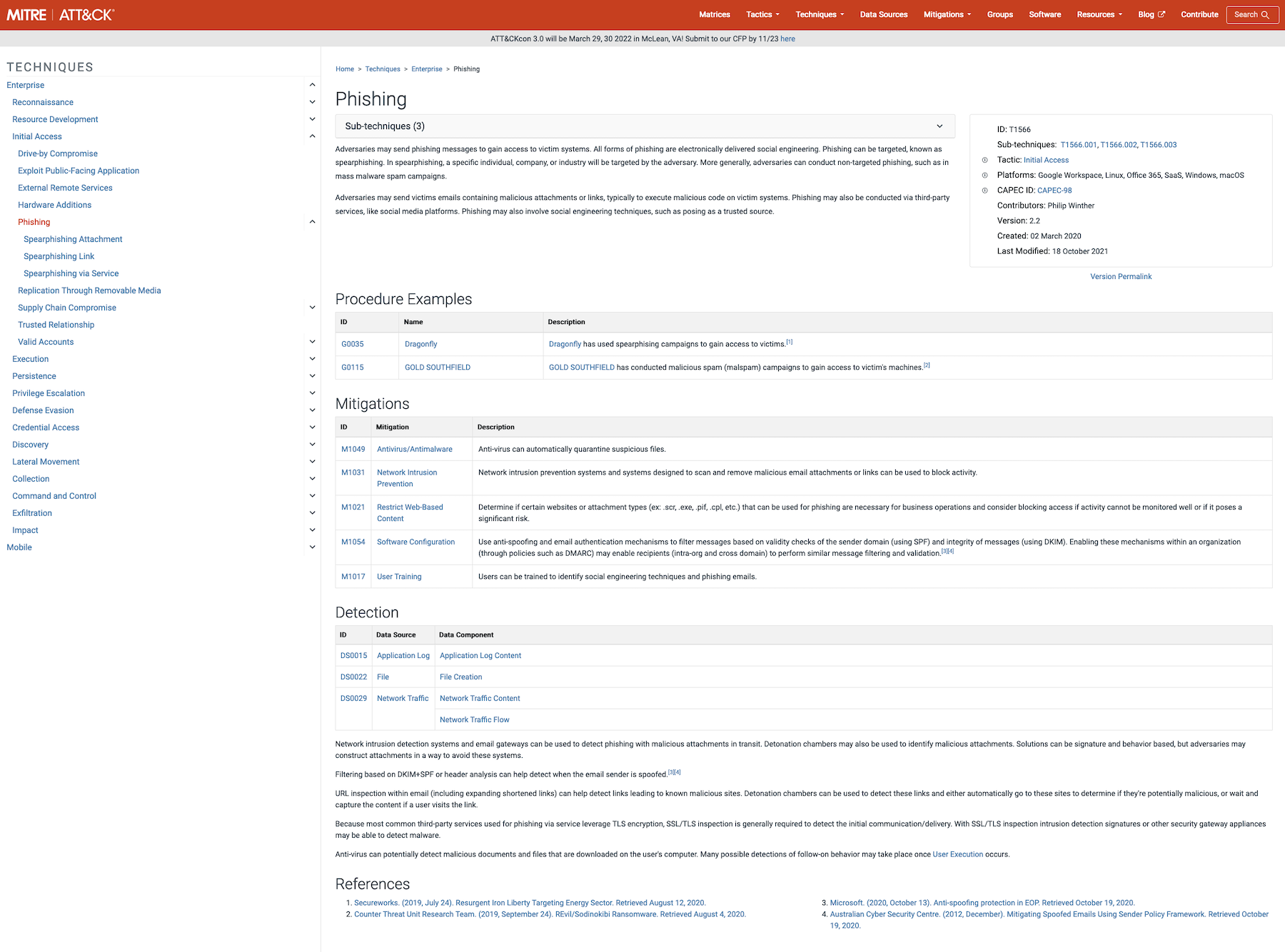 https://attack.mitre.org/techniques/T1566/
https://attack.mitre.org/techniques/T1566/
So how is all this information helpful? There are many different ways organizations can begin to use this information; a few are noted below:
- You have to often think like your enemy to anticipate ways to attack you. ATT&CK having a vast amount of information related to APTs linked to actionable detection and mitigation information can help you improve the security of your environment against genuine threats.
- In defensive security, there is not a one-size-fits-all solution or product. ATT&CK can help you find holes in your defenses by evaluating tactics and techniques to see how adversaries may get around your current protections.
- When comparing multiple security products or solutions, having their controls and detection capabilities mapped against ATT&CK can help highlight each’s strengths and weaknesses.
- Red team penetration testers can use ATT&CK to coordinate exercises and highlight deficiencies against targets, allowing for an easily consumable reference for defenders on where to improve.
- And, it goes without saying that ATT&CK is extremely helpful in Cyber Threat Intelligence to communicate how an adversary will behave and attack your organization.
MITRE Engage
The Engage framework, formally known as Shield, takes some of the same principles as ATT&CK but shifts in purpose. Instead of strictly mapping adversary tactics and techniques, Engage seeks to build specific matrices to help organizations achieve their defensive goals through “adversary engagement, deception and denial activities” (MITRE, 2021d). Like ATT&CK, Engage derives from real-world adversaries and is available online: https://engage.mitre.org/matrix/.
At the top level are the Goals, which MITRE describes as broad objectives an organization is looking to accomplish: https://engage.mitre.org/goals/. Each goal is divided into Strategic and Engagement goals, depending on their purpose:
Strategic
| ID | Name | Description |
|---|---|---|
| SGO0001 | Prepare | Help the defender think about what they want to accomplish with operations. |
| SGO0002 | Understand | Make sure that the defender is capturing, utilizing, and refining knowledge learned to improve the defender’s posture. |
Engagement
| ID | Name | Description |
|---|---|---|
| EGO0001 | Expose | Reveal the presence of ongoing adversary operations. |
| EGO0002 | Affect | Negatively impact the adversaries operations. |
| EGO0003 | Elicit | Learn about adversaries tactics, techniques, and procedures. |
Each goal is informed by approaches made up of activities, giving a familiar hierarchical structure. What’s makes this valuable is not only does it provide good organization, but each activity also maps back to ATT&CK!
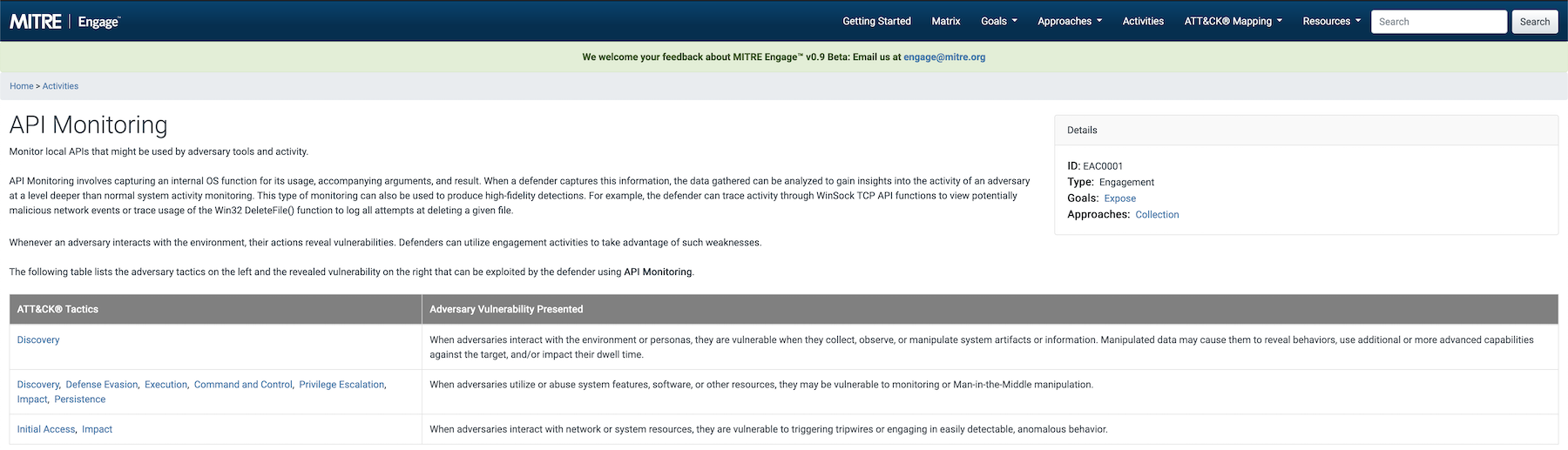 https://engage.mitre.org/activities/EAC0001/
https://engage.mitre.org/activities/EAC0001/
MITRE D3FEND
The last MITRE framework we will be discussing today (but certainly not the least) is D3FEND. As with the first two MITRE frameworks, this one is also freely available online and has mappings back to ATT&CK: https://d3fend.mitre.org/.
MITRE describes D3FEND as “… a catalog of defensive cybersecurity techniques and their relationships to offensive/adversary techniques” (MITRE, 2021a).
ATT&CK focuses on offensive tactics, techniques, and procedures, while D3FEND helps defenders effectively communicate defense techniques. The broad categories used in D3FEND to help strengthen an organization’s defense capabilities are Harden, Detect, Isolate, Deceive and Evict. Each one has specific techniques and sub techniques that map back to ATT&CK offensive techniques. Each D3FEND technique defines a concept or control without necessarily describing the implementation. This is intentional and serves to provide common language and terms that transcend vendor or technology.
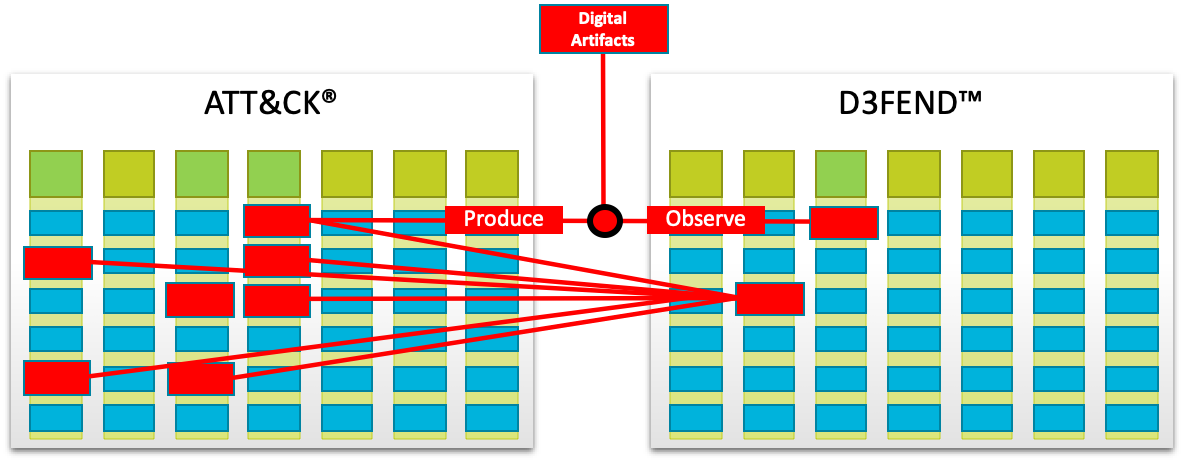 https://d3fend.mitre.org/about
https://d3fend.mitre.org/about
Defending Against Threat Actors
All three of these frameworks can help different industries better defend themselves from adversaries who are likely to target them. For example, if you worked at a business that was a contractor to the Defense Department of the United States, you may need to be aware of the APT groups that target businesses like yours. You could pull up the MITRE Groups catalog and look across all the identified actors for those known to focus defense contractors, allowing you to determine their TTPs and compare it to your current state.
You may find of interest APT17 who use Microsoft TechNet profiles as C2 infrastructure or Thrip who leverage LogMeIn for remote access, both of which could potentially target your company.
We will focus on a group that executed a high-profile attack earlier this year for this exercise.
HAFNIUM
HAFNIUM is a Chinese nation-state group tracked by Microsoft targeting US businesses, including Defense contractors, to perform espionage by exfiltrating sensitive information that could be valuable to other nations’ intelligence or economics (Burt, 2021). So far, the only attack attributed to HAFNIUM to date involves the abuse of an Exchange 0-days in early 2021 (Microsoft 365 Defender Threat Intelligence Team, 2021).
Exchange 0-day
In this attack against unpatched Exchange servers, of which belonged to tens of thousands of victims, HAFNIUM exploited several vulnerabilities which allowed for complete compromise of the target Exchange server:
| CVE | Base Score | Description |
|---|---|---|
| CVE-2021-26855 | 9.1 | A server-side request forgery (SSRF) vulnerability in Exchange which allowed the attacker to send arbitrary HTTP requests and authenticate as the Exchange server. |
| CVE-2021-26857 | 7.8 | An insecure deserialization vulnerability in the Unified Messaging service. Insecure deserialization is where untrusted user-controllable data is deserialized by a program. Exploiting this vulnerability gave HAFNIUM the ability to run code as SYSTEM on the Exchange server. This requires administrator permission or another vulnerability to exploit. |
| CVE-2021-26858 | 7.8 | A post-authentication arbitrary file write vulnerability in Exchange. If HAFNIUM could authenticate with the Exchange server then they could use this vulnerability to write a file to any path on the server. They could authenticate by exploiting the CVE-2021-26855 SSRF vulnerability or by compromising a legitimate admin’s credentials. |
| CVE-2021-27065 | 7.8 | A post-authentication arbitrary file write vulnerability in Exchange. If HAFNIUM could authenticate with the Exchange server then they could use this vulnerability to write a file to any path on the server. They could authenticate by exploiting the CVE-2021-26855 SSRF vulnerability or by compromising a legitimate admin’s credentials. |
ATT&CK
Exploring the MITRE Group page for HAFNIUM, we can see how they operate beyond the vulnerabilities, including activities leading up to the attack and what they do after the attack was successful. For example, once HAFNIUM exploited an Exchange server, among many other things, they’d typically utilize procdump to dump LSASS from memory, which is a sub-technique under OS Credential Dumping. MITRE ATT&CK has this mapped as T1003.001. Following the trail to the technique’s page, we can see how it works, why it works, and what an attack utilizing it would look like. There is then a list of linked Groups that are also known to use this technique and a section for both mitigations and detection. There’s plenty of information within ATT&CK alone to help you begin to harden your environment against LSASS dumping, but as we covered earlier, there’s more than just ATT&CK available from MITRE.
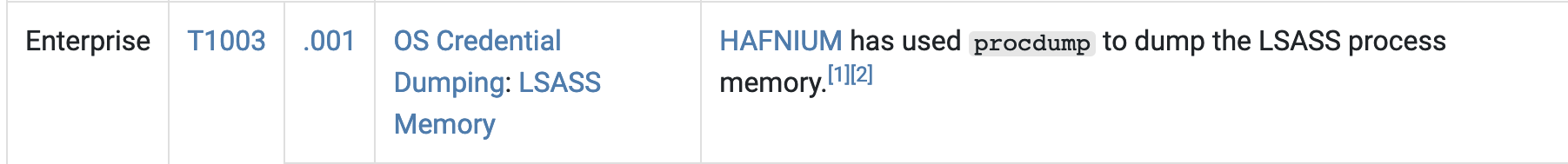 https://attack.mitre.org/groups/G0125/
https://attack.mitre.org/groups/G0125/
DEFEND
If we pivot over to MITRE D3FEND, we can see what has been mapped to T1003.001. Searching for it generates an interactive web that shows how LSASS is linked with other artifacts and techniques and opportunities to evict, detect, isolate, or deceive.
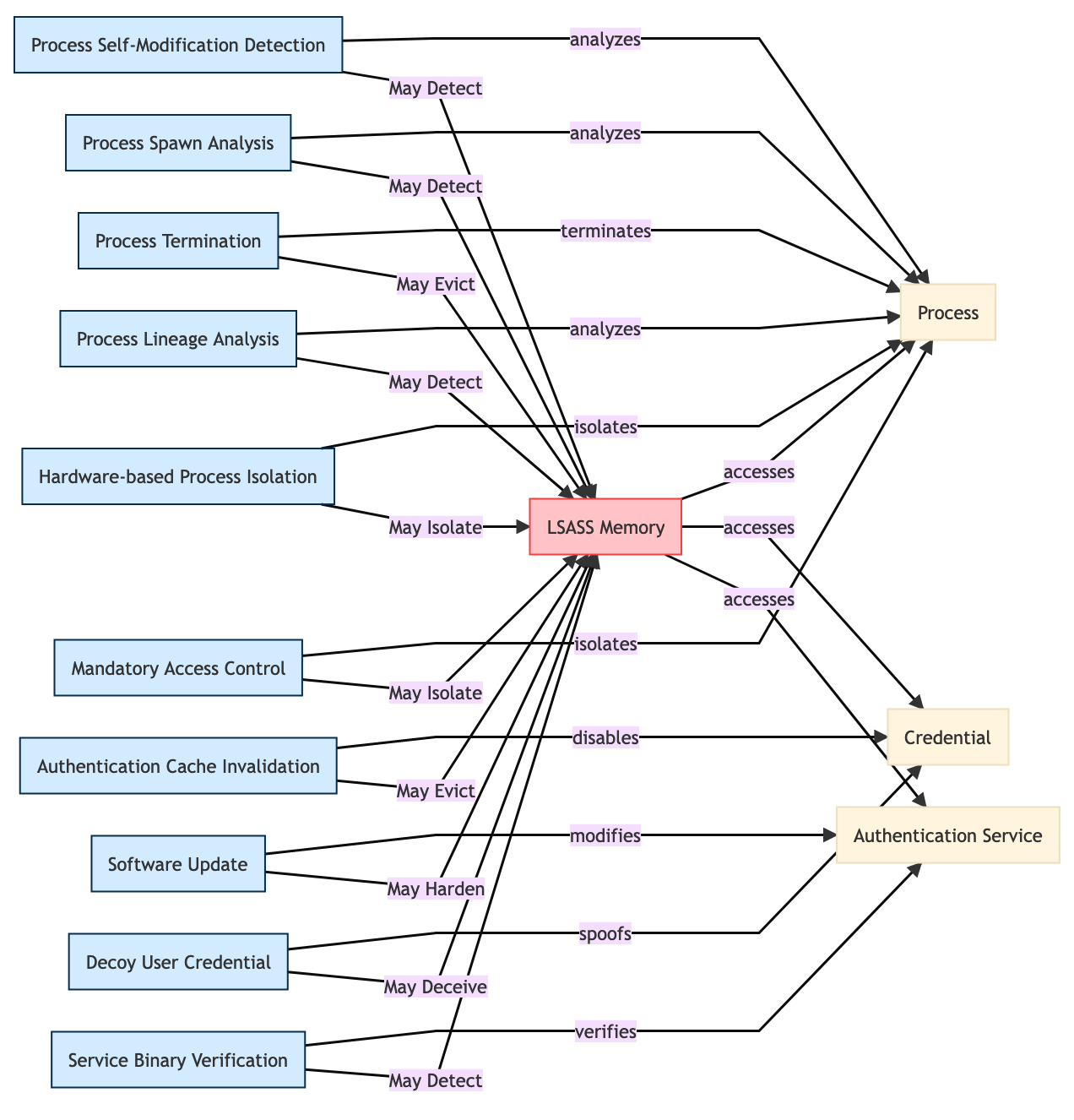 https://d3fend.mitre.org/offensive-technique/attack/T1003.001
https://d3fend.mitre.org/offensive-technique/attack/T1003.001
Engage
Similarly, we can look for the OS Credential Dumping mapping in MITRE Engage to learn how to take action against our adversary or support our operational strategies.
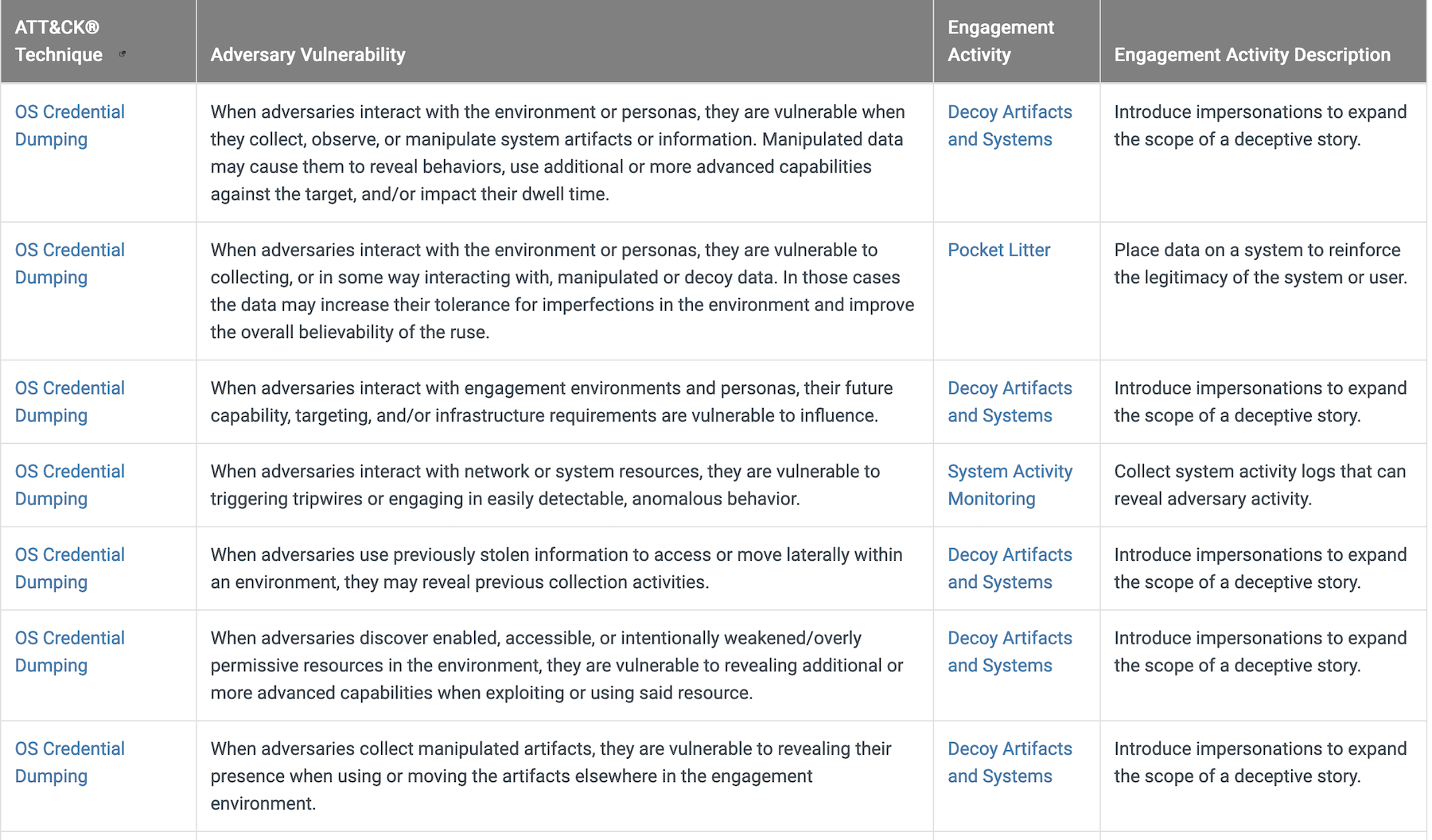 https://engage.mitre.org/attack_mapping/TA0006/
https://engage.mitre.org/attack_mapping/TA0006/
Just think about how much information is covered between the three portals without researching LSASS and credential dumping by yourself. Even if the frameworks don’t wholly encompass 100% of your needs, it’s still a reliable starting point that can give you a head start.
IOCs
Since we’re on the subject of HAFNIUM, it doesn’t hurt to include the IOCs associated with this attack for good measure. Microsoft did a pretty good job making as many resources available surrounding this attack as possible to help victims identify and recover from a breach.
On their blog post, under Attack details, is a breakdown of post-exploitation behavior and other resources to identify compromise. Microsoft even provided a scanning tool to assist checking for IOCs associated with each vulnerability: https://github.com/microsoft/CSS-Exchange/tree/main/Security
Activities
In general, on Exchange servers you would want to look for the following activities:
- Procdump execution
- 7zip execution
- Add-PSSnapin to install Exchange PowerShell
- Powershell creating a new net socket object
- Powershell downloading PowerCat from Github to connect to a remote server
Web Shell Hashes
- b75f163ca9b9240bf4b37ad92bc7556b40a17e27c2b8ed5c8991385fe07d17d0
- 097549cf7d0f76f0d99edf8b2d91c60977fd6a96e4b8c3c94b0b1733dc026d3e
- 2b6f1ebb2208e93ade4a6424555d6a8341fd6d9f60c25e44afe11008f5c1aad1
- 65149e036fff06026d80ac9ad4d156332822dc93142cf1a122b1841ec8de34b5
- 511df0e2df9bfa5521b588cc4bb5f8c5a321801b803394ebc493db1ef3c78fa1
- 4edc7770464a14f54d17f36dc9d0fe854f68b346b27b35a6f5839adf1f13f8ea
- 811157f9c7003ba8d17b45eb3cf09bef2cecd2701cedb675274949296a6a183d
- 1631a90eb5395c4e19c7dbcbf611bbe6444ff312eb7937e286e4637cb9e72944
Web Shell Paths
C:\inetpub\wwwroot\aspnet_client\C:\inetpub\wwwroot\aspnet_client\system_web\- In Microsoft Exchange Server installation paths such as:
%PROGRAMFILES%\Microsoft\Exchange Server\V15\FrontEnd\HttpProxy\owa\auth\C:\Exchange\FrontEnd\HttpProxy\owa\auth\
With any of the following filenames:
- web.aspx
- help.aspx
- document.aspx
- errorEE.aspx
- errorEEE.aspx
- errorEW.aspx
- errorFF.aspx
- healthcheck.aspx
- aspnet_www.aspx
- aspnet_client.aspx
- xx.aspx
- shell.aspx
- aspnet_iisstart.aspx
- one.aspx
LSASS Dump Files
LSASS dump files in either directory:
C:\windows\temp\C:\root\
References
- Anomali. (n.d.). What Is MITRE ATT&CK and How Is It Useful? www.anomali.com. https://www.anomali.com/resources/what-mitre-attck-is-and-how-it-is-useful
- Burt, T. (2021, March 2). New nation-state cyberattacks. Microsoft on the Issues. https://blogs.microsoft.com/on-the-issues/2021/03/02/new-nation-state-cyberattacks/
- Microsoft 365 Defender Threat Intelligence Team. (2021, March 2). HAFNIUM targeting Exchange Servers with 0-day exploits. Microsoft Security. https://www.microsoft.com/security/blog/2021/03/02/hafnium-targeting-exchange-servers/
- MITRE. (2021a). About. D3fend.mitre.org. https://d3fend.mitre.org/about
- MITRE. (2021b). Goals. Engage.mitre.org. https://engage.mitre.org/goals/
- MITRE. (2021c). MITRE ATT&CKTM. Mitre.org. https://attack.mitre.org/
- MITRE. (2021d). MITRE Engage. Engage.mitre.org. https://engage.mitre.org/resources/getting-started