Cyber Threat Intelligence Sharing
Table of Contents
Different organizations within the same industry will have different cyber defense capabilities for researching, detecting, and stopping threats. Government entities have another set of capabilities that private sectors do not. An organization trying to defend itself from advanced persistent threats does no good working in a bubble if other organizations deal with the same threats. The modern-day internet and technology stacks that businesses rely upon globally were built upon an open and shared foundation, so why should threat intelligence be any different? Cyber Threat Intelligence (CTI) sharing can help bridge the gap between multiple organizations, uniting intelligence efforts to make their industry more resilient to threats and identifying attacks and trends in a more timely manner.
What is Cyber Threat Intelligence Sharing?
There are two main types of Cyber Threat Intelligence (CTI) sharing: unidirectional and bidirectional. We’ve previously discussed forms of unidirectional sharing, that is, where it’s a one-way feed of CTI from a source to recipients with no individual contribution fed back. This can be a free or paid external source that an organization may subscribe to, or it could be internally developed CTI produced and shared within the walls of a single organization.
Bidirectional is the process of collaborating with other organizations to build a curated list of CTI for the benefit of the group, typically where every member is encouraged to contribute but not required to do so. The end goal of both types of sharing is the same – detect and stop threats before it’s too late.
An organization may have some reservations about sharing CTI with outside parties. Threat Intelligence platform Anomali outlines a few of these concerns and what you can do to overcome them:
- Privacy and liability concerns
- Taking necessary precautions to remove proprietary or sensitive data from shared information
- Have legal counsel review laws and regulations to identify what types of information are protected and which are not
- Not enough valuable information to share
- As mentioned previously, not every organization will observe the same attacks. Any amount of sharing, big or small, can help the industry develop a more clear picture of the threat landscape and identify trends.
- Not enough experience to share
- Similar to the previous point, every little bit helps. Plus, the contribution might spark discussion within the group or have more seasoned resources interested in providing suggestions to help mature your organization.
- Prematurely disclosing a breach
- Anomali suggests that by following CTI sharing best practices, you can avoid revealing more information than your organization is comfortable sharing.
If you want to start collaborating on shared CTI from scratch, there are a few standards you can build from. NIST offers an outline on how to begin an information-sharing capability within an organization.
- Know what sources you have internally that can produce intelligence to share.
- Have goals and objectives that align with your security operations and policies.
- Figure out how to share the information externally.
- Identify peers and partners to exchange information with, building trust between all parties. aaa Again, check out the NIST “Guide to Cyber Threat Information Sharing” for a concise resource on all things CTI sharing.
The truth is, not every organization needs to put in the time and effort to stand up an information-sharing group. An Information Sharing and Analysis Center (ISAC) may exist for your vertical and already offer a platform to coordinate CTI sharing.
ISACs
Information Sharing and Analysis Centers (ISACs) are a group within the non-profit National Council of ISACs that focus on a specific industry identified by the Department of Homeland Security as critical infrastructure. Banking, infrastructure, research, defense, energy, healthcare all have their ISACs, to name a few. The goal is to facilitate bidirectional intelligence sharing between members of an industry and as a way for the government to disseminate information selectively with the private sector. Through law enforcement and national intelligence activities, ISACs can provide members with potentially more complete information than what might be found from other sources.
Selection
If an organization wanted to join an ISAC, a good starting point would be to visit the member ISACs page on the National ISACs website. Here you can search for the industry that applies to your organization. In this example, we are a defense contractor, so we would be interested in the National Defense ISAC (ND-ISAC).
Benefits
Examining the membership criteria on ND-ISAC’s website, our example defense contractor organization seems to be eligible: “ND-ISAC membership is available to all defense sector organizations, suppliers, contractors and their interdependent entities…” Once the organization has decided to join the ND-ISAC, it must fill out an application to begin the review process.
ND-ISAC lists the membership benefits as:
- Access to all-hazards threat intelligence
- Secure peer-to-peer and community-to-community collaboration
- Mentoring relationships with mature security teams
- Shared services and resources
- Threat information
- Best practices
- DFARS compliance assistance
- Alerts, notifications, and warnings on relevant threats to the industry
- Latest government threat advisories and recommendations
- Cybersecurity analyst training opportunities'
- Defense industry-focused working groups
- Service offerings geared for DIB companies and their suppliers
It’s great to see that besides the obvious benefits of joining an ISAC for CTI sharing, there are also some discounted services available to members to help them improve their defenses, including training and security products.
Cost
While the membership fees are not posted publicly, it’s safe to say an organization in the defense industry should contact the ND-ISAC to start a discussion around membership to see if enough value is provided to justify the fees. Many members-only events are seen as networking opportunities outside of pure CTI, so there are multiple layers of benefits associated with being a member organization.
APT17: Deputy Dog
APT17, aka Deputy Dog, is a Chinese threat group that has targeted “U.S. government entities, the defense industry, law firms, information technology companies, mining companies, and non-government organizations” (FireEye & Microsoft, 2015). Tracked by FireEye and Microsoft around 2015, Deputy Dog used some pretty innovative techniques to obfuscate command and control activities with the group’s preferred malware: BLACKCOFFEE – capable of creating reverse shells, uploading or downloading files, enumerating files and processes on the victim host, or extending functionality through subsequent instructions sent via shellcode.
Deputy Dog set up Microsoft TechNet accounts posing as forum users, and within the profiles of these users, they encoded IP addresses to be used for command and control. BLACKCOFFEE would connect to the webpage of a random Deputy Dog TechNet profile to get instructed on which IP to beacon to. From a security monitoring perspective, at the network layer, BLACKCOFEE would initially generate traffic to Microsoft TechNet, lower the suspicion of compromise, and make it harder to identify the command and control IP from binary analysis alone.
Game of Thrones Campaign
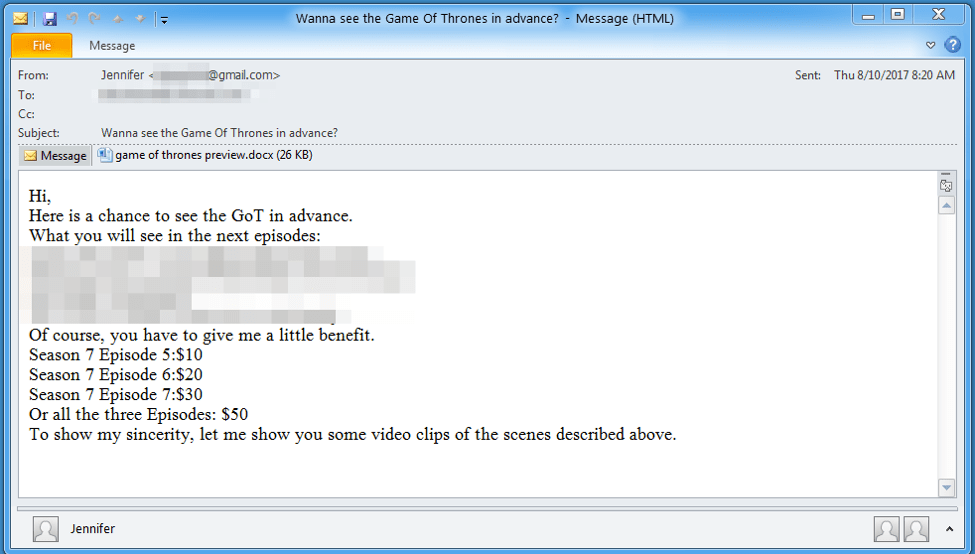
One of the more notable attacks carried about by Deputy Dog involved capitalizing on the popularity of Game of Thrones at the time to deliver malware via targeted phishing attacks, piggybacking off of actual Game of Thrones leaks that occurred due to a hack at HBO. They would send an email pretending to sell leaked episodes, hoping people would be tempted enough to open the attachment, which claimed to be a preview.
Of course, the attachment was a Word doc with an embedded .lnk object which would download and run the infamous 9002 RAT, another favorite tool used by Chinese groups.
BLACKCOFFEE IOCs
Indicators to monitor for related to BLACKCOFFEE malware used by Deputy Dog
MD5
- de56eb5046e518e266e67585afa34612
- 195ade342a6a4ea0a58cfbfb43dc64cb
- 4c21336dad66ebed2f7ee45d41e6cada
- 0370002227619c205402c48bde4332f6
- ac169b7d4708c6fa7fee9be5f7576414
- 5f2fcba8bd42712d9975da208a1cc0ca
- 5d16e5ee1cc571125ab1c44ecd47a04a
- da88e711e4ffc7c617986fc585bce305
- c016af303b5729e57d0e6563b3c51be4
- 0b757d3dc43dab594262579226842531
Domains
- translate[.]wordraference[.]com
- news[.]jusched[.]net
IP Addresses
- 130[.]184[.]156[.]62
- 69[.]80[.]72[.]165
- 110[.]45[.]151[.]43
- 121[.]101[.]73[.]231
- 103[.]250[.]72[.]39
- 148[.]251[.]71[.]75
- 217[.]198[.]143[.]40
- 178[.]62[.]20[.]110
- 175[.]126[.]104[.]175
- 103[.]250[.]72[.]254
- 1[.]234[.]52[.]111
GoT 9002 RAT IOCs
SHA256
- 9e49d214e2325597b6d648780cf8980f4cc16811b21f586308e3e9866f40d1cd
- 5a678529aea9195b787be8c788ef4bb03e38e425ad6d0c9fafd44ed03aa46b65
- efdb6351ac3902b18535fcd30432e98ffa2d8bc4224bdb3aba7f8ca0f44cec79
- bdd695363117ba9fb23a7cbcd484d79e7a469c11ab9a6e2ad9a50c678097f100
- 192e8925589fa9a7f64cba04817c180e6f26ad080bf0f966a63a3280766b066a
URLs
- hxxp[://]27[.]255[.]83[.]3/x/
- hxxp[://]27[.]255[.]83[.]3/y/
IP Addresses
- 27[.]255[.]83[.]3
References
- Anomali. (2021). Sharing Threat Intelligence. Anomali. https://www.anomali.com/resources/sharing-threat-intelligence
- FireEye, & Microsoft. (2015, May). Hiding in Plain Sight: FireEye and Microsoft Expose Obfuscation Tactic. https://www2.fireeye.com/rs/fireye/images/APT17_Report.pdf
- Johnson, C. S., Badger, M. L., Waltermire, D. A., Snyder, J., & Skorupka, C. (2016). Guide to Cyber Threat Information Sharing. https://doi.org/10.6028/nist.sp.800-150
- National Council of ISACs. (2019). https://www.nationalisacs.org/
- National Defense Information Sharing and Analysis Center (NDISAC). (n.d.). National Defense ISAC. https://ndisac.org/
- Paganini, P. (2017, August 28). Chinese APT17 group leverages fake Game of Thrones leaks as lures. Security Affairs. https://securityaffairs.co/wordpress/62376/apt/apt17-hbo-hack.html
- Proofpoint. (2017, August 25). Operation RAT Cook: Chinese APT actors use fake Game of Thrones leaks as lures. Proofpoint. https://www.proofpoint.com/us/threat-insight/post/operation-rat-cook-chinese-apt-actors-use-fake-game-thrones-leaks-lures